Hello Py
字符串搜索特征字符串,
比如flag、right、wrong、!,然后找到了如下的代码、
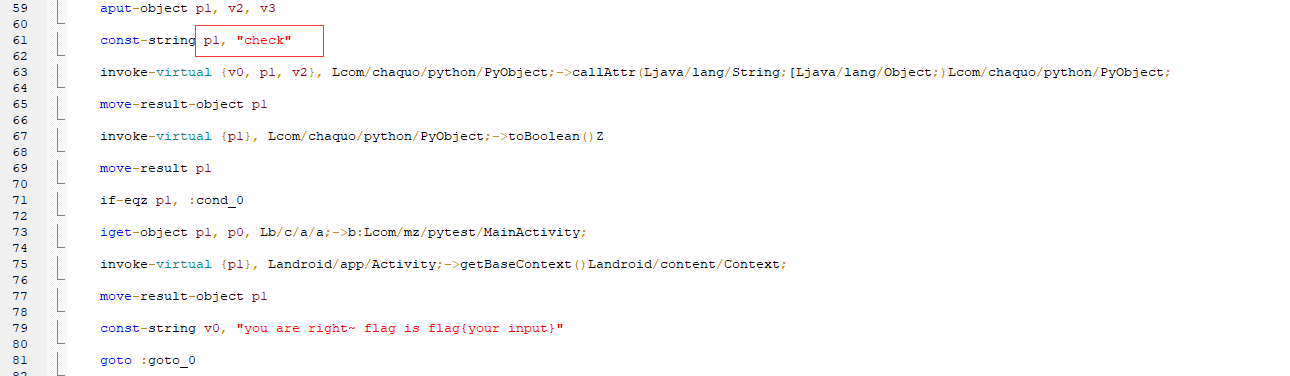
p1的值决定了flag是否正确。
确定关键虚拟函数。
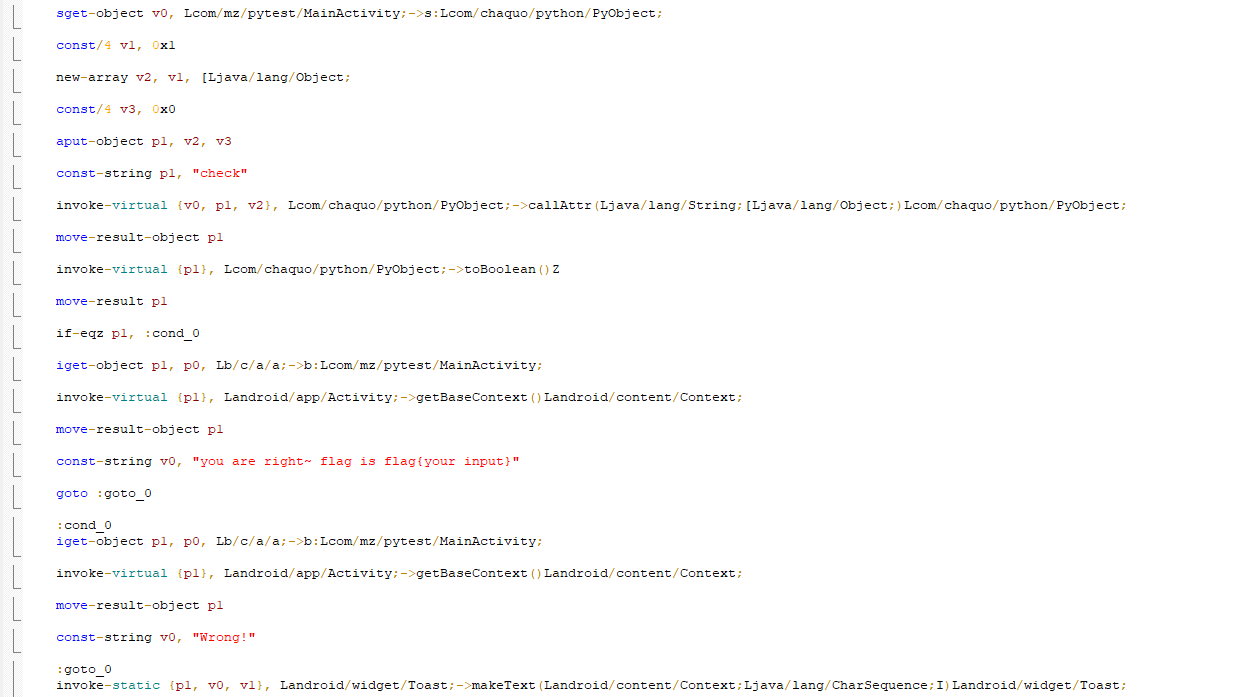
关键逻辑check在Python代码;
Lcom/chaquo/python/PyObject;看了一圈什么内容都没有,py文件应该在其他文件里;
使用jax反编译,然后在AndroidPlatform.java文件里,发现有释放文件和删除文件操作。
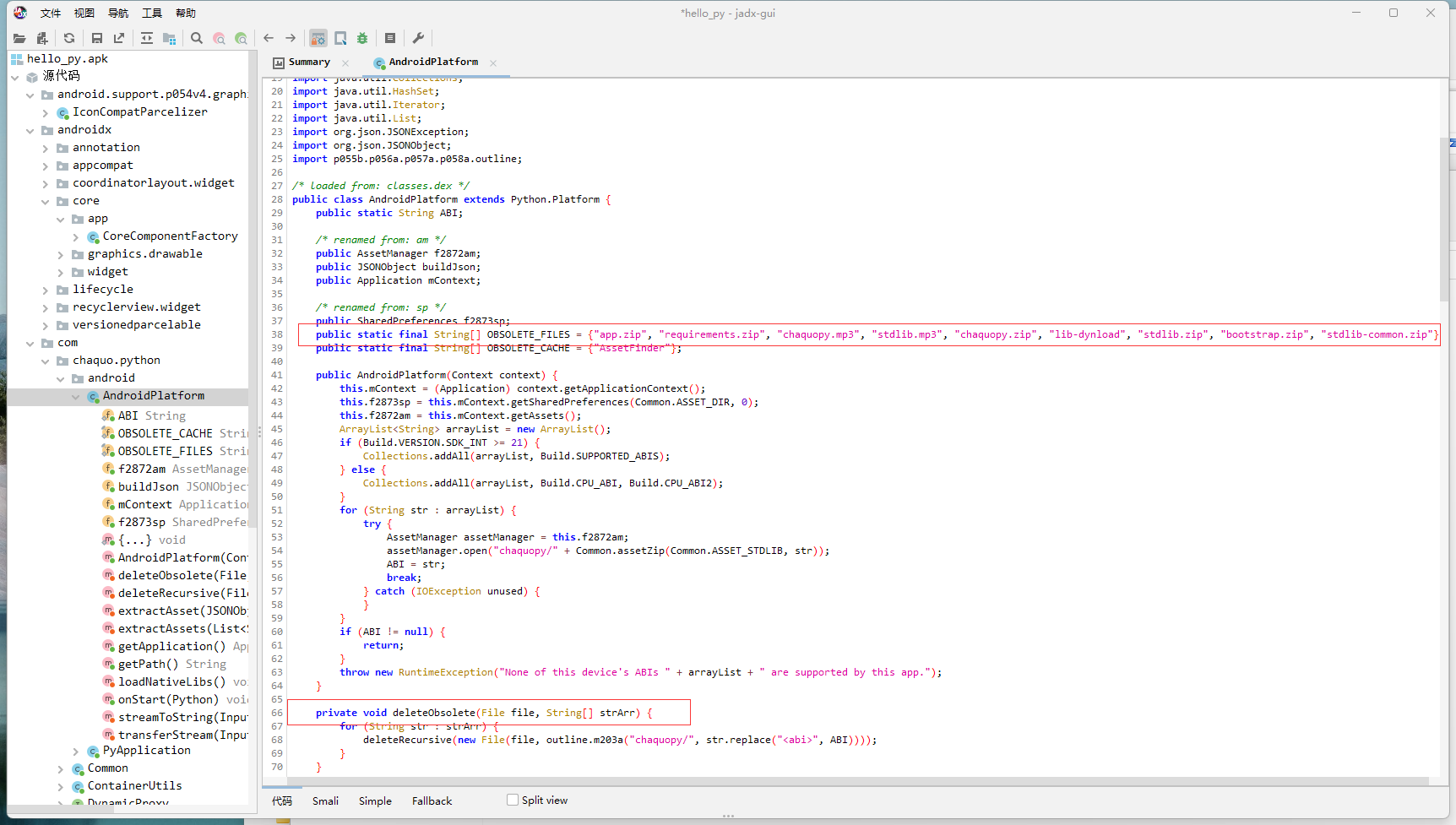
修改smali代码,让它不要删文件。
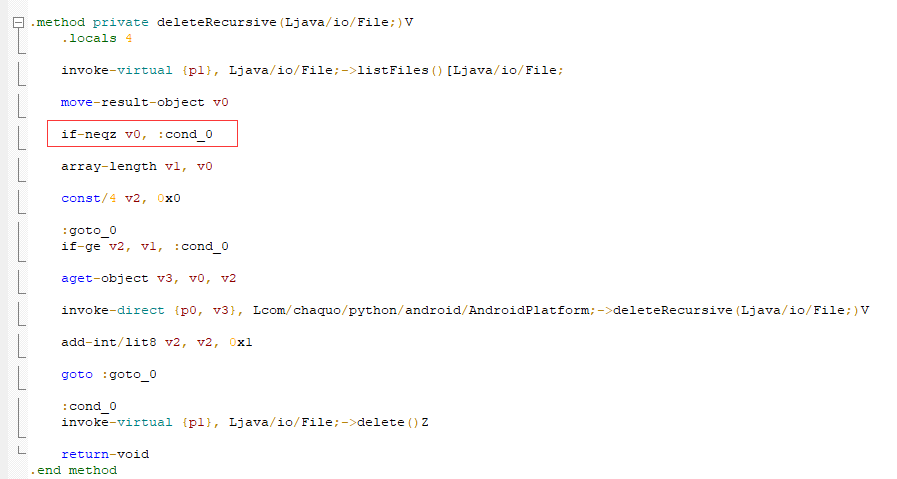
发现编译失败,我的环境不行;
没办法,去资源目录里,突然看到app.yml居然没有被删除,可以直接读取,把它修改为zip后缀,然后解压得到hello.py文件。
1 |
|
一开始想手写解密脚本,不知道为什么总是出错,解密出的值都是不可见字符,放弃。去csdn上找了一个公开的脚本:
链接如下:
https://blog.csdn.net/A951860555/article/details/120120400
1 |
|
得到最终flag,b’c1f8ace6-4b46-4931-b25b-a1010a89c592’
URL从哪儿来
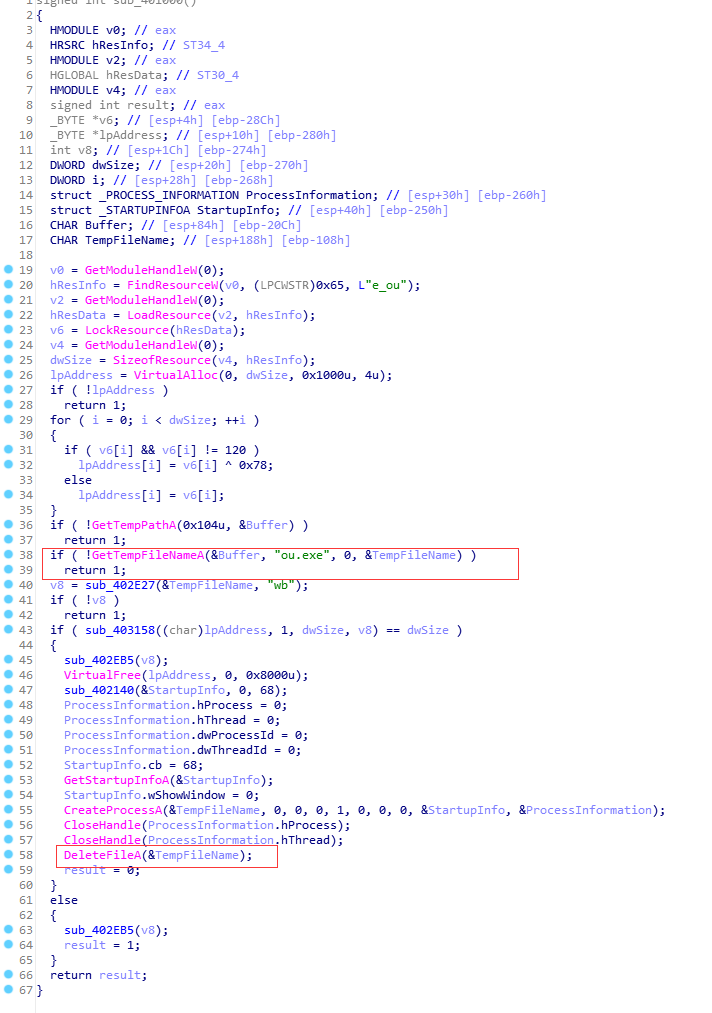
不想在自己电脑上运行,丢沙箱里,结果沙箱不给文件。没办法,自己下Api断点,获取文件。
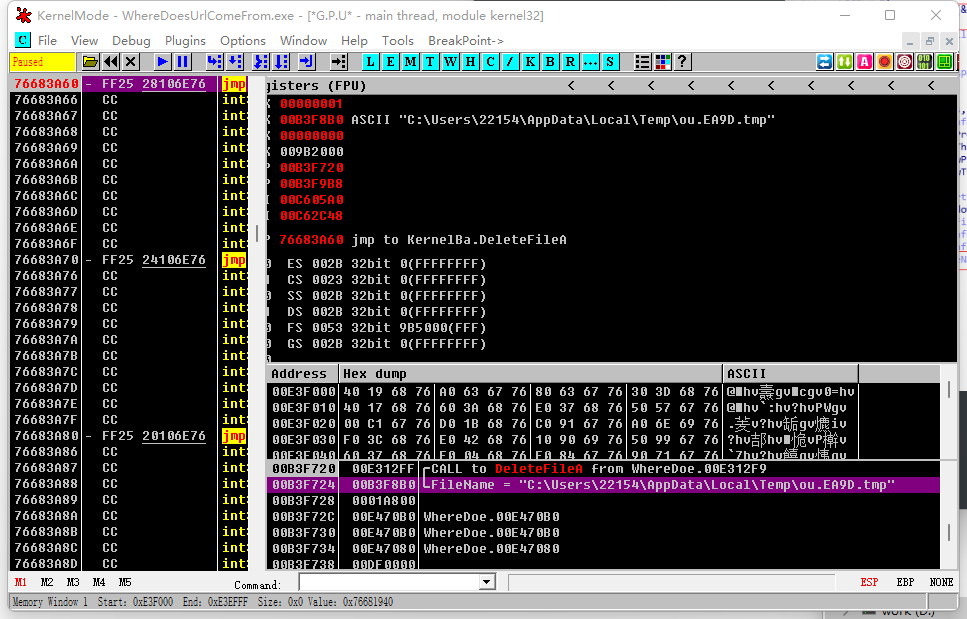
获取到文件后,strings发现有base64特征,动态加载后观察,发现关键判断函数。
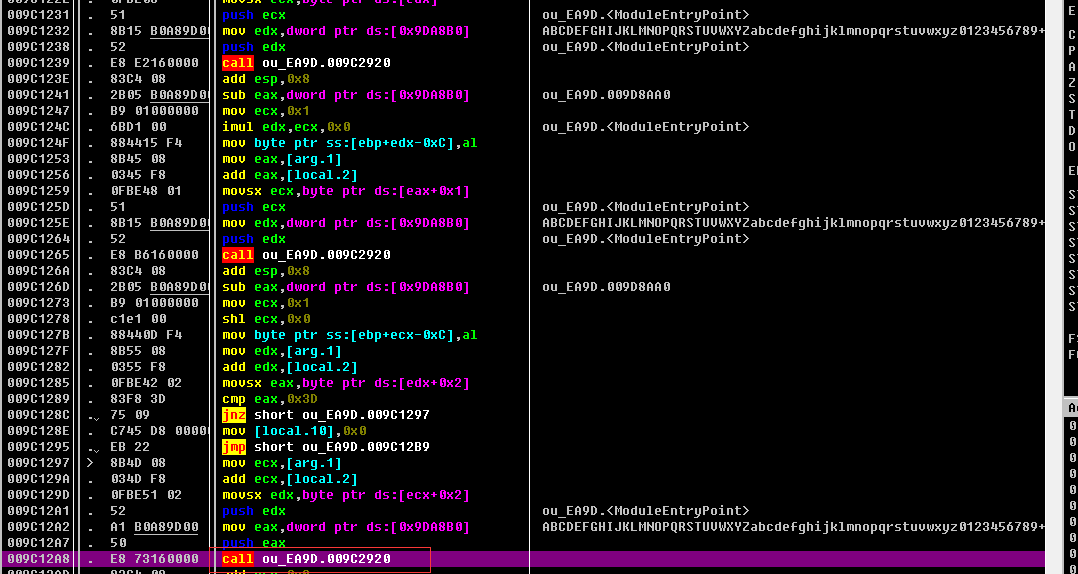
001DF654 |006D7838 ASCII “ZmxhZ3s2NDY5NjE2ZS02MzY5LTYyNmYtNzE2OS03NDYxNzA2MTc3NjF9”
尝试b64解码,
flag{6469616e-6369-626f-7169-746170617761}
发现里面有flag,提交成功。